Current Research Topics
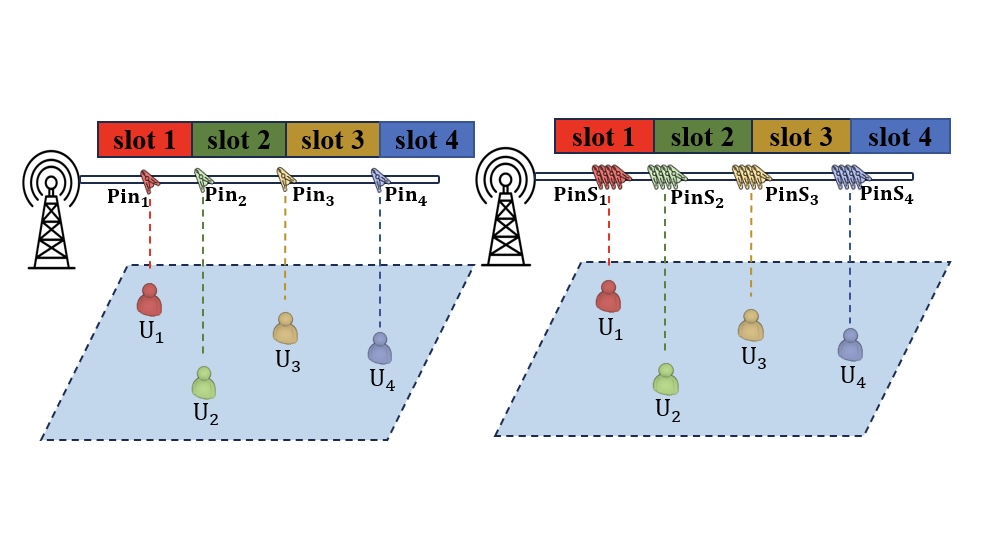
Pinching Antenna Systems
Pinching antenna technology is a promising direction in flexible-antenna systems, offering a low-cost and reconfigurable approach to improve wireless communication. Unlike traditional antennas with fixed positions, pinching antennas are created by placing small dielectric elements along a dielectric waveguide. This setup allows antennas to be positioned close to users, which helps establish strong line-of-sight links and reduce large-scale path loss. The system supports multiple antennas on a single waveguide at no extra hardware cost and aligns well with techniques like non-orthogonal multiple access (NOMA) by enabling signal superposition. With the ability to adjust antenna placement to reconfigure channel conditions, pinching antennas provide an efficient and scalable solution for future wireless networks, especially in indoor and dense-user scenarios. In this project, we aim to investigate: 1) Low-complexity optimization of pinching antenna placement; 2) Blockage model in pinching antenna assisted networks; 3) AI-empowered pinching antenna systems
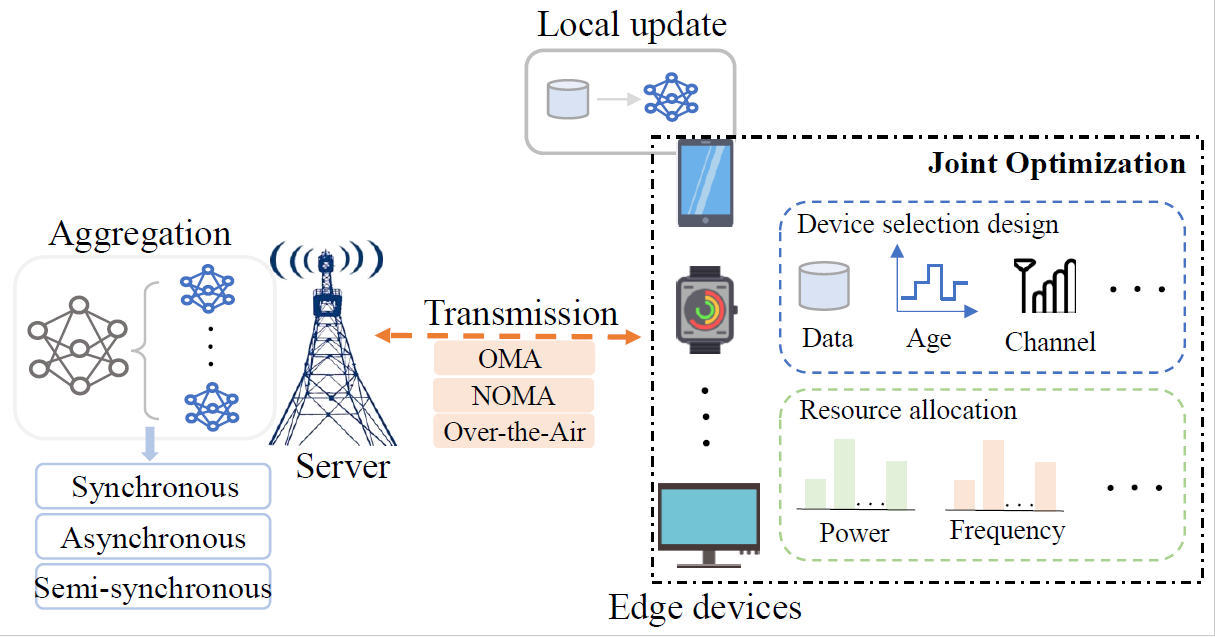
Communication-Efficient Edge AI
Edge artificial intelligence (AI), a fusion of edge computing and AI algorithms, has attracted significant research interest in recent years. Unlike traditional cloud-based AI, which relies on centralized processing of raw data, edge AI enables distributed data processing and decision-making directly at the device level, effectively mitigating the risk of data leakage. Additionally, edge AI offers reduced latency and improved energy efficiency, making it well-suited for responsive applications such as industrial IoT, autonomous vehicles, and smart home systems. In edge AI systems, devices perform local model training using their own data and upload the trained model parameters to a coordinating server responsible for global model aggregation and distribution. However, the frequent parameter exchange between devices and the server poses challenges to communication and training efficiency, which are critical to the performance of edge AI systems. This project aims to explore communication-efficient and task-oriented edge AI systems, focusing on the following key aspects: 1) Communication-efficient Federated Learning (FL)(Link) and Hierarchical FL (HFL)(Link) over NOMA Networks: Investigating strategies to optimize communication overhead in FL and HFL frameworks operating in NOMA networks. 2) Digital Twin-Assisted FL Systems: Leveraging digital twin technology to enhance training efficiency and improve resource utilization[3 vtc][4 twc](Link1,Link2). 3) Task-Oriented Edge AI Systems: Designing edge AI solutions tailored to diverse task requirements across various devices to ensure optimal performance and resource allocation.(Link)
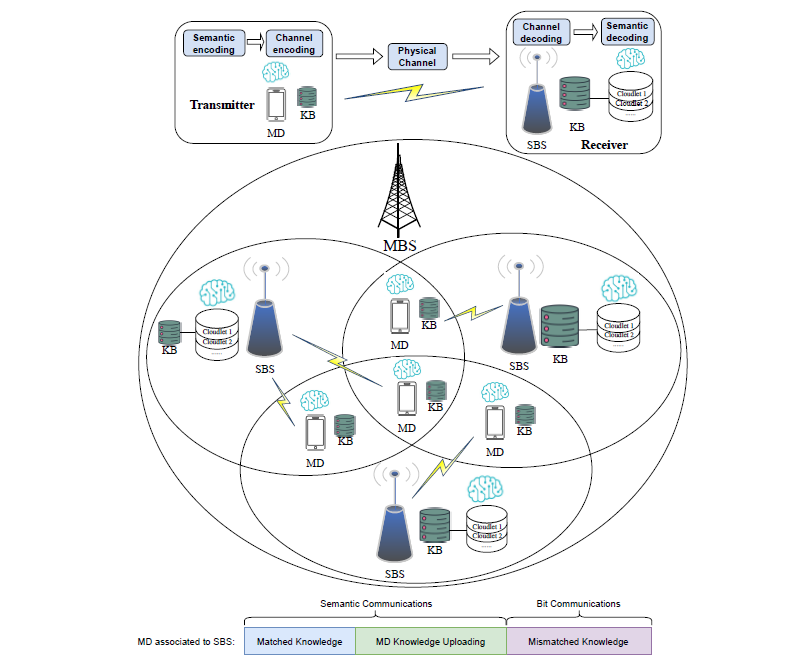
Semantic Communications
Benefitting from advancements in micro-electronics and artificial intelligence, recent developments in machine learning and end-to-end communication technologies are driving the transformation of traditional communication systems toward future paradigms. Semantic communications, as an emerging intelligent communication paradigm, focus on exchanging the meaning or semantics extracted from messages rather than transmitting the raw bit stream messages directly. By leveraging shared knowledge bases (KBs) between the transmitter and receiver, more meaningful semantic information is extracted from the source data prior to undergoing semantic and channel encoding at the transmitter. The receiver can recover the source information by semantic restoration from the received semantic data through channel and semantic decoding. This approach has shown significant potential to address spectrum scarcity and improve communication efficiency, garnering growing attention from both industry and academia. In this project, we will investigate 1) a novel edge-assisted semantic communications framework for resource-constrained IoT devices. To the best of our knowledge, this is the first work to study the semantic extraction model selection problem in an edge-assisted semantic network(Link); 2) a knowledge sharing-enabled task-oriented hybrid semantic-bit communications mechanism for multi-cell networks to tackle the KB mismatch challenge(Link); 3) a collaborative knowledge sharing-empowered semantic-bit communications mechanism to maximize the generalized effective semantic transmission rate we derived in two-tier edge networks, to overcome the mobile device power limit and harsh channel conditions(Link).
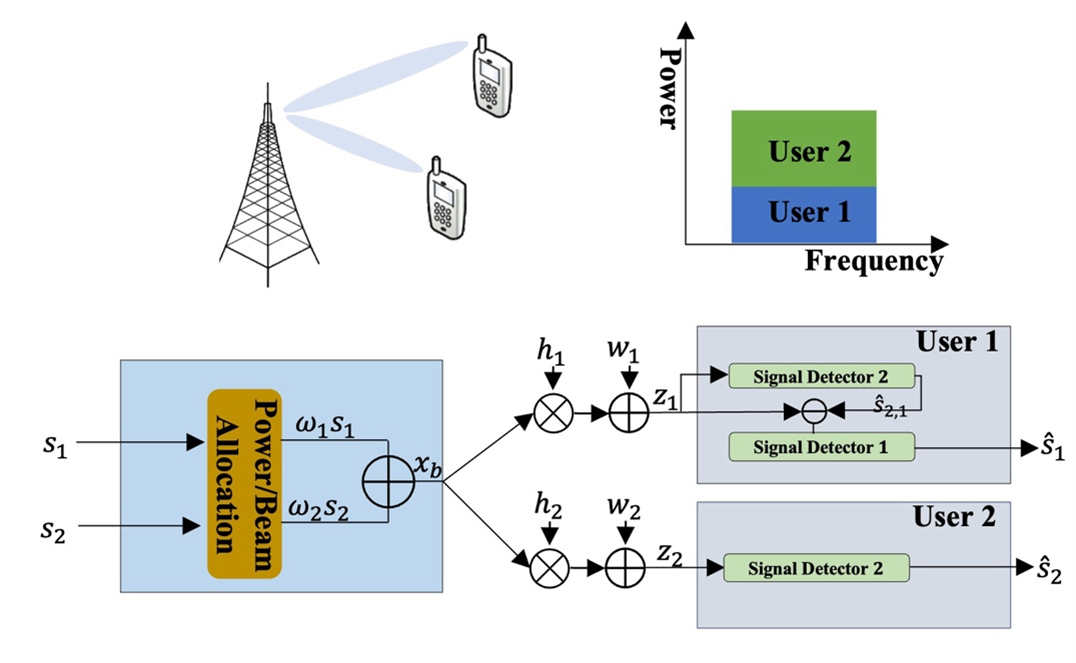
Non-Orthogonal Multiple Access (NOMA) Communications
Non-Orthogonal Multiple Access (NOMA), recently introduced for the 3rd Generation Partnership Project Long-Term Evolution Advanced (3GPP-LTE-A), presents a promising solution to the challenges faced by 5G networks by enabling multiple users to share the same orthogonal resource block. This approach significantly improves spectrum efficiency compared to traditional Orthogonal Multiple Access (OMA) methods. As a result, it has attracted considerable research interest. The key idea behind NOMA is to exploit differences in users' channel conditions. By allocating different power levels to users based on their channel quality, NOMA ensures that signals intended for different users can be effectively separated using successive interference cancellation (SIC) at the receiver. This enables high-priority users with better channel conditions to decode their signals first while allowing users with weaker channels to access the same resources. In this project, we aim to investigate the performance gain introduced by NOMA 1) Optimization of beamforming, phase adjustment, and power distribution in a multi-cluster RIS-NOMA System 2) Minimization of power consumption in downlink hybrid NOMA networks 3) Minimization of power consumption in a semantic and bit-based users coexisting NOMA networks.
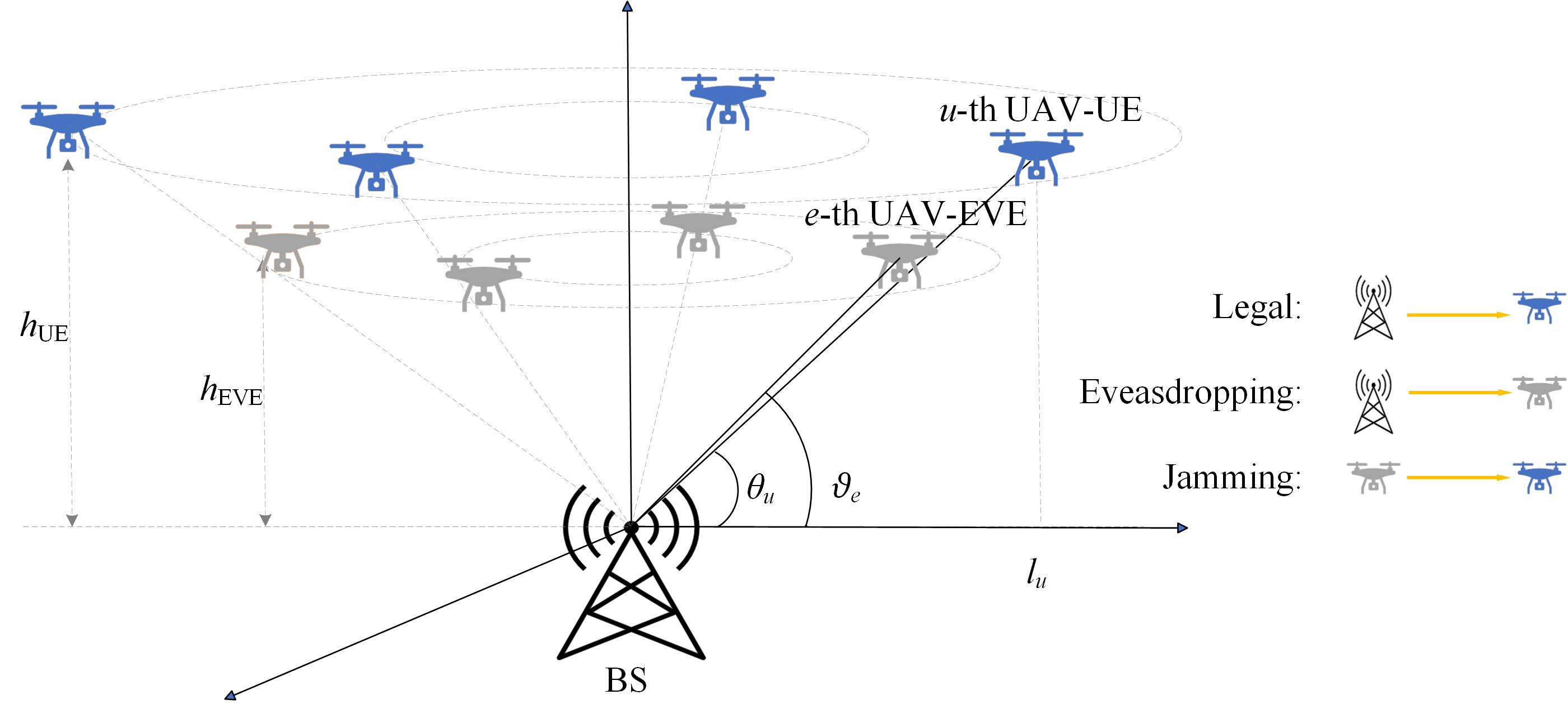
Trustworthy Wireless Communications
Secure wireless communications face the increasing vulnerabilities caused by the open nature of propagation environments, requiring capability of rejecting unauthorized access and protecting signal from eavesdropping. To address above two security issues, various mechanisms at physical layer are proposed to be potential solutions with advantages of low latency and high compatibility. Specifically, artificial noise (AN) and precoding (beamforming) can differentiate legitimate and illegitimate transmission receptions to achieve secrecy rate, and authentication is to verify transceivers based on hardware impairments, channel characteristics, or artificial fingerprint (tag). Comprehensive secrecy achieving and authentication enhancement cooperatively provide fundamentals for communication security and information confidentiality. In this project, to ensure trustworthy communications, we propose several potential methods to comprehensively achieve both secrecy and authentication: 1): creating a dual-reference symmetric tag as the reference for one-time pad encryption and the reference for tag embedding authentication, 2): extracting accuracy channel attributes for key generation and channel-based authentication, 3) designing uniquely decomposable constellation with cooperative message and tag transmission.
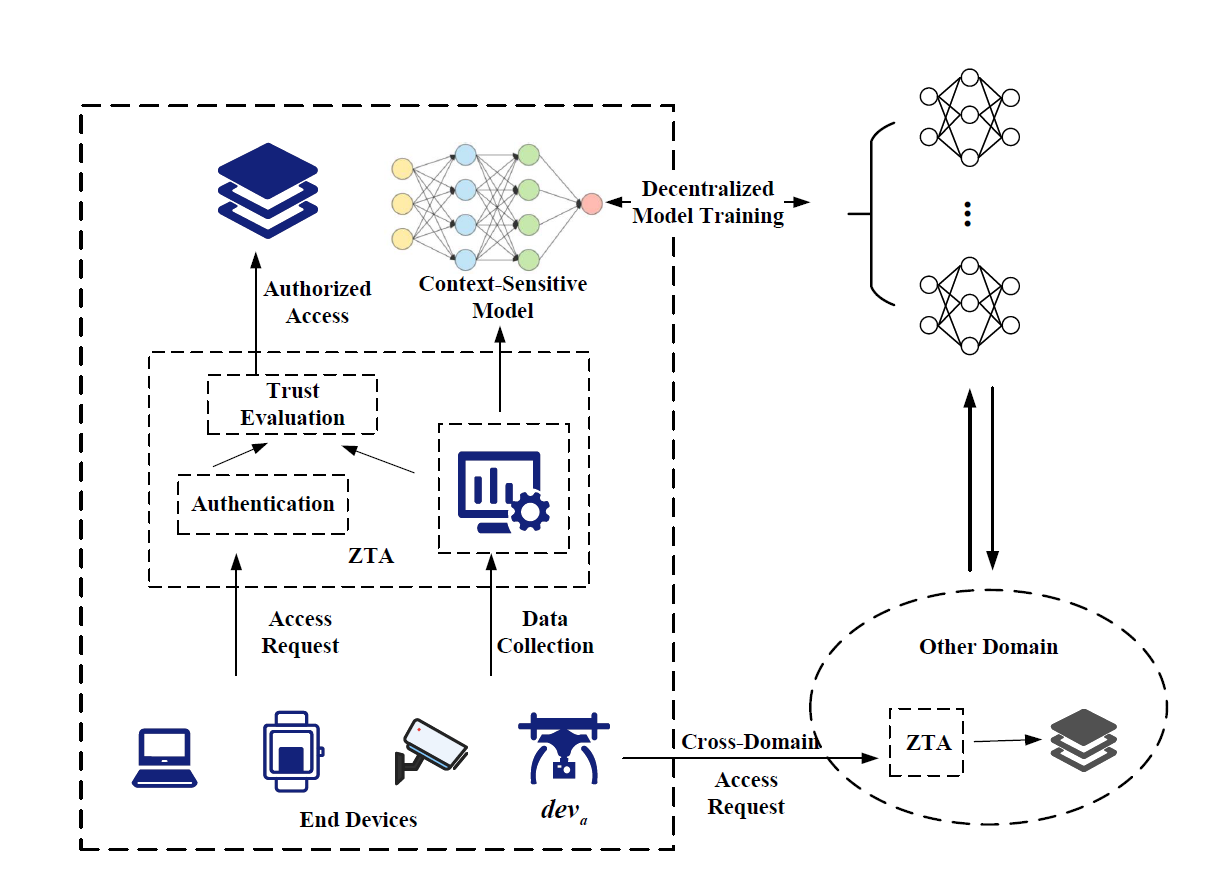
Decentralized Zero Trust Authentication and Authorization
Decentralized Zero Trust Authentication and Authorization is an innovative framework designed to enhance the security of large-scale IoT networks. Unlike traditional centralized methods that rely on one-time authentication, it leverages the principles of Zero Trust Architecture (ZTA) to ensure continuous device verification and fine-grained access control, effectively mitigating risks such as lateral movement attacks and session hijacking. By decentralizing control and integrating context-aware decision-making, this framework dynamically adapts to evolving device behaviors and environmental factors, offering a more secure and flexible authentication solution. However, implementing decentralized authentication and authorization systems poses challenges, including ensuring efficient communication across domains, preserving data privacy, and adapting to the diverse data characteristics inherent in large-scale IoT networks. These challenges necessitate innovative mechanisms to optimize performance, reduce network load, and enhance security without compromising privacy or efficiency. This project focuses on advancing decentralized zero trust authentication and authorization through the following research objectives: 1) Continuous and decentralized access control for both intra-domain and cross-domain IoT environments. 2) Development of privacy-preserving mechanisms that reduce data transmission by securely sharing essential information, enhancing efficiency without compromising data security. 3) Real-time adaptability to diverse network conditions through dynamic, context-aware evaluation methods and collaborative learning techniques, such as Decentralized Federated Learning (DFL), to support secure and efficient cross-domain authorization processes.
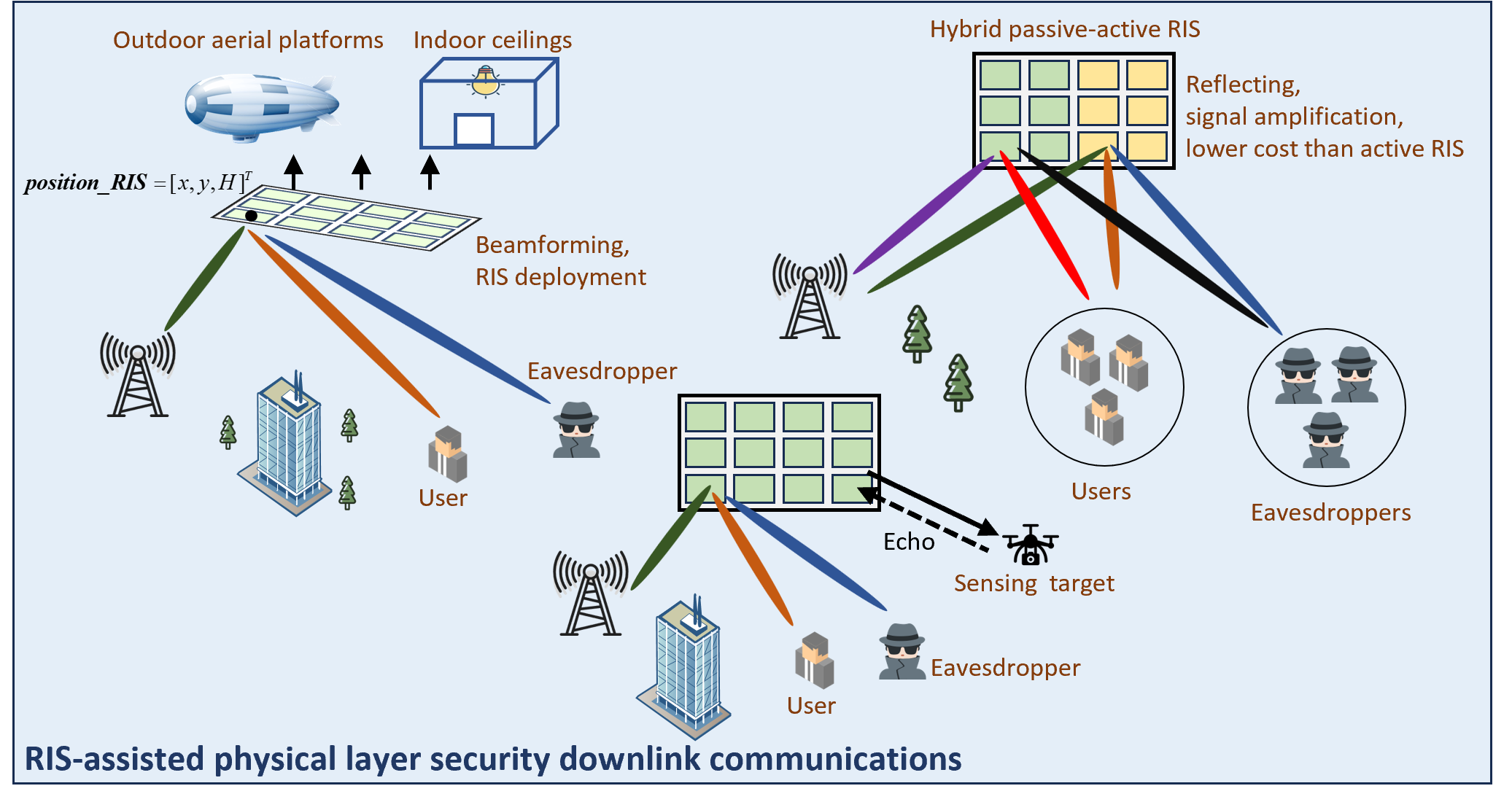
Reconfigurable intelligent surfaces (RISs)
Sixth-generation (6G) networks suffer from serious security risks due to the broadcasting characteristics of wireless channels, a large amount of privacy-sensitive data, and the exponential growth of attack vectors. However, physical layer security (PLS) is an effective method of securing legitimate transmissions by exploiting the dynamic characteristics of wireless communications. Fortunately, reconfigurable intelligent surfaces (RISs) have transformed traditional wireless networks into smart radio environments without incurring huge costs and increasing complexity, enabling a new network paradigm by providing power-efficient, cost-effective services with high data rates for 6G networks. Besides, the RIS-aided PLS solutions can be flexibly applied to vital 6G technologies, such as multi-access edge computing (MEC), integrated sensing and communication (ISAC), and NOMA. In the project, the RIS-aided PLS communication systems are designed. Specifically, I will 1) introduce the beamforming design of the passive RIS-aided PLS communication system, with considering the spatial location deployment of the RIS. 2) explore the ability of hybrid active/passive RIS to enhance system secure performance. 3) considering the realistic requirements, use RISs to enhance the secure performance of integrated sensing and communication (ISAC).